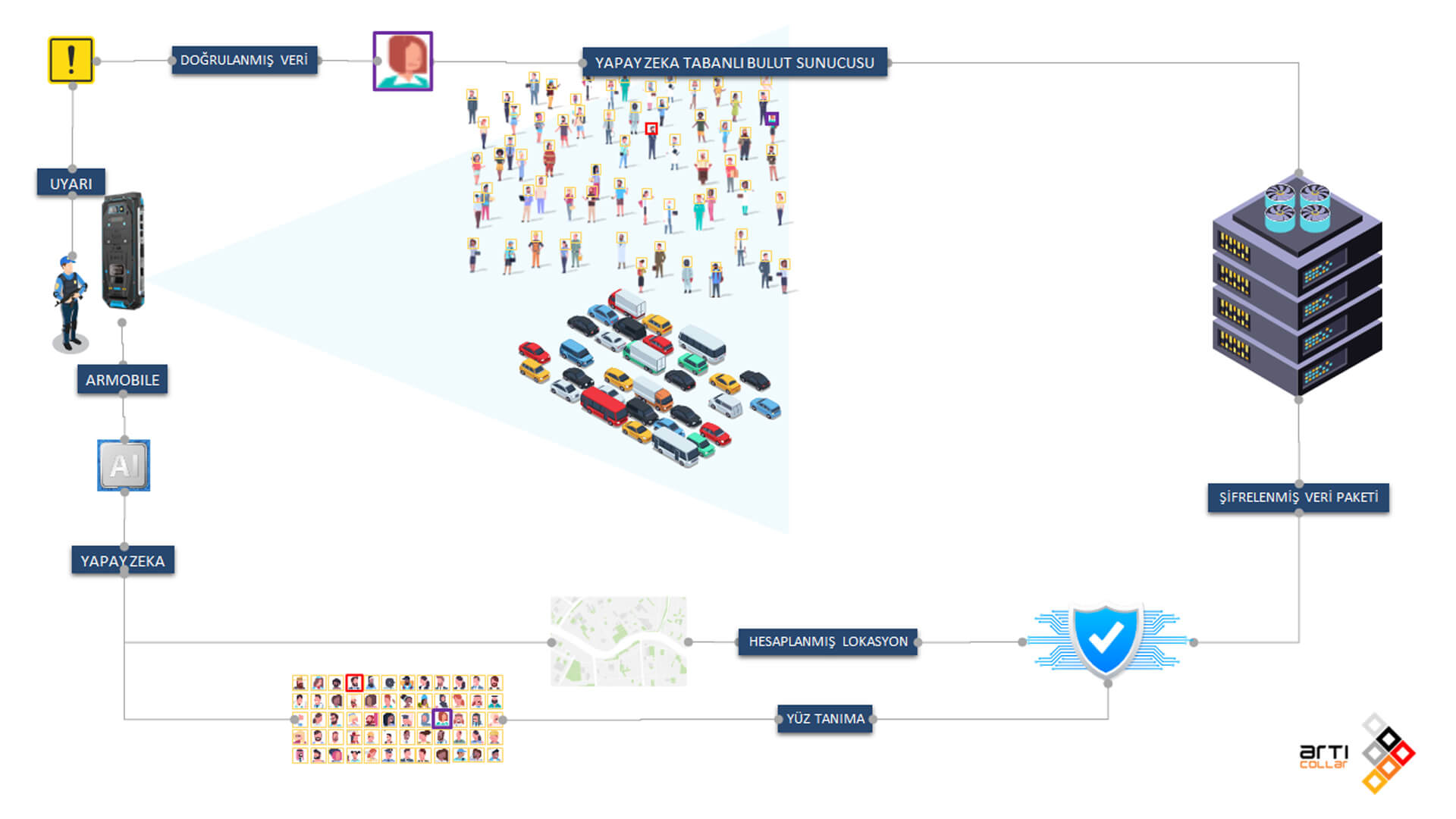
With our Articollar project developed in the field of urban security, we create instant alerts and locate individuals being sought using a specially developed phone attached to law enforcement officers. Thanks to the artificial intelligence chips on the phone, we can perform real-time facial recognition without transmitting the image to the center.

With this device, which has been researched and developed by our team for many years, you can run artificial vision algorithms with active zoom support up to 40 meters. At the same time, you can perform all the functions of a regular phone. With this device, which we have equipped with end-to-end hardware-based encryption, you can communicate with the center using push-to-talk. GPS and GLONASS support, high-speed connection with 4G and 5G, and effective viewing angle with micro gimbal are available. The gimbal can be moved on 2 axes.
Facial recognition is applied to the images obtained from the camera. Additionally, the location is recorded in real-time thanks to the GPS chip. The system, which processes the distance to detected faces with location data, estimates the target’s location.
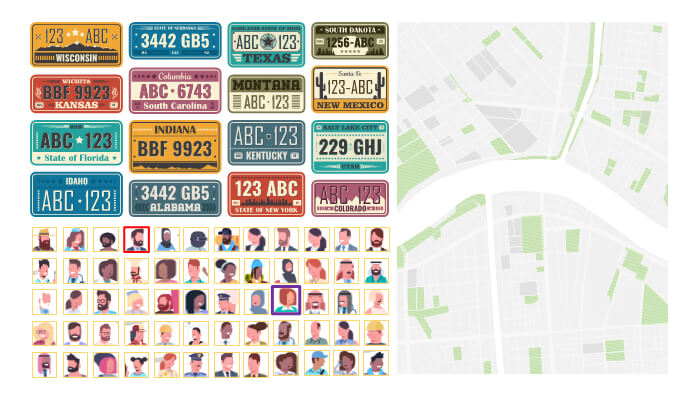

Facial recognition is performed in three stages. In the first stage, all faces in the image are detected, and the detected faces are digitized into a vector. The generated vector is sent to the server for comparison. If the necessary hardware is available on the server, we process a face among 40 million faces in 1ms or less. It compares with the faces of individuals already in the system and finds the most similar person. The identified person and real-time facial information are displayed on the operator’s screen for approval.
All GPS movements of law enforcement officers are recorded in real-time and transmitted to the center. Real-time tracking can be performed on the map in the central management panel. Additionally, when facial recognition algorithms detect a target, the distance between the officer and the target is calculated using image processing algorithms and added to the current location, and the estimated target location is transmitted to the center.

End-to-end encryption is a method where data is encrypted by the device sending it to the server, in a way that can only be decrypted on the server. The message travels encrypted from the sender to the server. With mutual key exchange, no one intercepting can access the data.
In an E2EE system, encryption keys should only be known by the parties involved in the communication. To achieve this, E2EE systems can encrypt data using a pre-shared secret key (PGP) or a one-time key derived from a pre-shared secret key (DUKPT), known as a pre-arranged string of symbols. Additionally, they can agree to generate a key during communication using Diffie-Hellman key exchange (OTR).
If a detection is made above the verification rate determined by the operator at the end of the comparisons made on the server, it is submitted for the operator’s approval. The incoming facial image is shown to the operator in an interface along with the facial images stored in the system. Up to this stage, all detected faces are framed in yellow, turning to a red frame if resembling a wanted person, and if the operator approves, framed in purple. At this stage, an alert is sent to law enforcement with the location.